Developing a Culture of Skepticism – Matt Gardiner, CPA, CFE
One of the cornerstones of the audit profession is “Professional Skepticism”. The Generally Accepted Auditing Standards define this as “an attitude that includes a questioning mind and a critical assessment of audit evidence.” It’s this mindset that ensures auditors gather and examine evidence that supports the ultimate audit opinion. That mindset drives the decision making of employees across all industries. Encouraging your employees to practice professional skepticism in their day-to-day duties will improve security and reinforce the ethics you want in your organization.
As the world becomes increasingly reliant on technology each of us will encounter more instances where we need to be skeptical. Actions as simple as clicking the wrong link in an email, accidentally signing into a malicious web page that appears to be our intended destination, or utilizing an unsecure Wi-Fi network to access work or personal accounts can open the door for someone to take advantage of your organization’s or employees’ accounts.
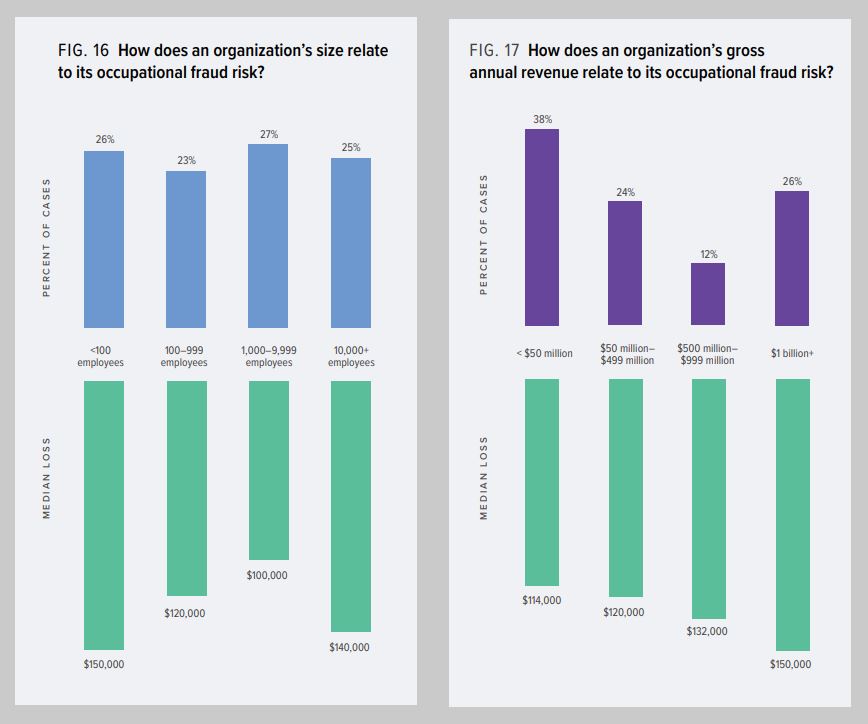
It’s easy to shrug off the risk of fraud: “It would never happen here!”, “No one would want to get into our system”, “Our risk is small!” The Association of Certified Fraud Examiners 2020 Report to the Nations revealed that while the amount per loss was lower for organizations with less than $50 million in annual revenues than those with greater than $50 million, 38% of all fraud cases come from those smaller organizations.
The belief that your organization is immune to the risk is what makes it so much more enticing for those with the intent to defraud your employees and organization of information and assets.
Examples of Common Threats
Frequently, victims are targeted to divulge logins and passwords through phishing attempts via email. Here’s how it works: the scammer sends an email which appears to come from a reputable site like Google or Microsoft, asking the victim to log into their account. The phishing email contains a link to a website which is identical to Google’s Gmail, and the victim enters their information into the site to log in. Instantly, the scammer has access to the victim’s account, and may be able to get into other accounts that the login combination is used for. Encouraging your staff to utilize multiple-factor authentication, employ different login and password combinations for each account, and to carefully examine the sender of emails received should help alleviate this threat.
Another common mistake made in our technology-dependent world is eagerly connecting to free Wi-Fi hotspots whenever out and about. Connecting to these networks can give access to your devices to other users in the network. If accessing sensitive websites such as your banking account or email, it may allow others in the area to see what was typed in and to capture login and password information, then gain access to those accounts.
Risks may not always be technical in nature. For instance, fraudulent invoices submitted to your organization can easily be generated which appear completely legitimate. These invoices may describe believable services which were never performed or product which was never delivered requesting payment. It’s important that your accounting system includes robust review and approval of invoices received and checks disbursed, and in addition that your staff is empowered to question the legitimacy of invoices received.
|
Best Practices & Recommendations
Source: www.DOL.gov (references below) |
Eliminate the Weak Link
Developing a culture of skepticism through regular risk assessments, fraud awareness training, and security discussions is pivotal in ensuring your staff stay vigilant in securing themselves and your organization. While establishing a secure system is important, at the end of the day humans can either be the strongest or the weakest link in the security chain; training is what makes the difference.
References:
Association of Certified Fraud Examiners. “2020 Report to the Nations”. www.ACFE.com. 2020. Web. https://www.acfe.com/report-to-the-nations/2020/
U.S. Department of Labor. “Online Security Tips”. www.DOL.gov. April 2021. Web. https://www.dol.gov/sites/dolgov/files/ebsa/key-topics/retirement-benefits/cybersecurity/online-security-tips.pdf
U.S. Department of Labor. “Cybersecurity Program Best Practices”. www.DOL.gov. April 2021. Web.

